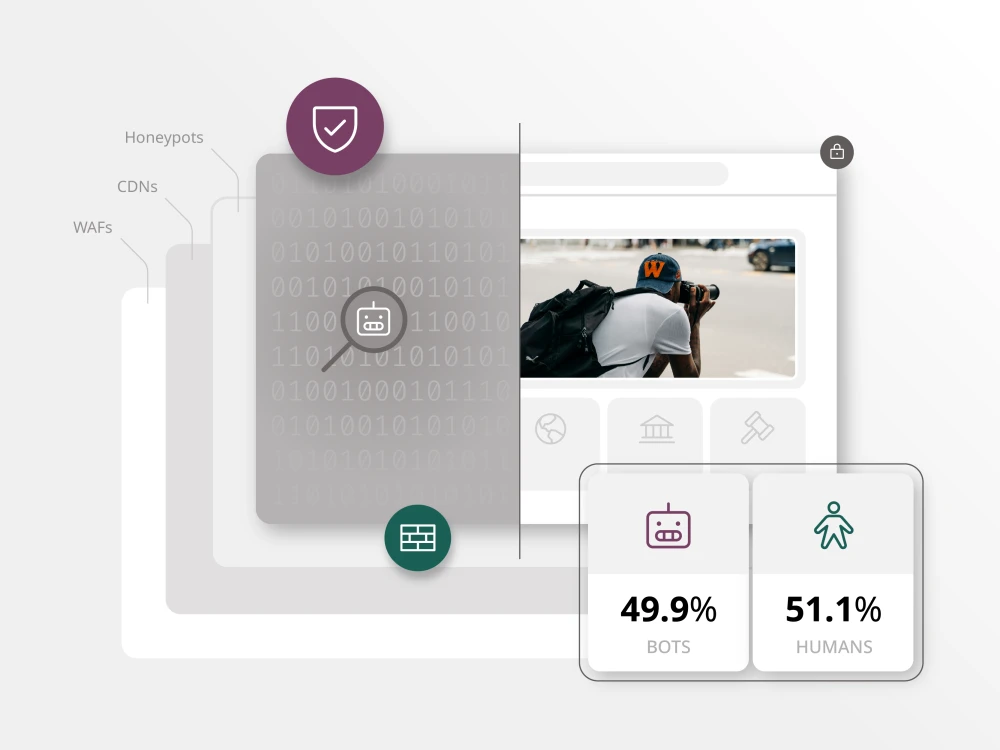
Security threats are escalating, and David Habib, Chief Information Officer at Brightspot, warns that organizations should prepare for a new wave of risks. He points to two major developments reshaping the landscape — cheaper, more accessible botnets and AI-enabled fraud at scale. Together, they are fueling three areas of elevated concern: insider threats, content misappropriation and volumetric attacks.
“Botnets are much more common now, which makes them cheaper. It’s basic economics,” Habib says. “AI is enabling bad actors to do things at scale that they used to do one at a time.”
The insider threat is the persistent first risk
According to Habib, insider threats remain the single greatest vulnerability facing organizations. This includes employees, contractors and vendors who already have — or can obtain — access to systems.
“Eighty percent — some studies say 99 percent — of cyber incidents begin with social engineering,” he explains, pointing to how phishing and other manipulative tactics open the door to breaches. AI, he warns, is only making these attacks more sophisticated and easier to scale.
Another troubling development is what Habib calls remote worker fraud: “You’re hiring someone, and you’re not getting who you think you are.” Deepfake job applicants and identity misrepresentation, he adds, are introducing fresh risks into already vulnerable environments.
Real-world examples show how damaging insiders can be when controls fail. One Brightspot customer discovered unfavorable content published to its production site after a former employee’s access had not been revoked. With overly broad network permissions still in place, that individual retained full rights to publish long after departure.
Habib’s advice is clear: organizations need to routinely review roles and access privileges, eliminate outliers and require at least two human approvers for high-risk changes. “Use role-based access control and require at least two human approvers for high-risk changes,” he stresses.
SSO and OneLogin help you track who holds the keys to your CMS — and take them back the moment access is no longer needed.
Content misappropriation
Organizations are also facing a surge in automated bots systematically copying websites for purposes ranging from training AI models to launching fraudulent lookalike sites.
Habib describes it as a uniquely personal type of threat: “We’re seeing at least as many, if not more, bots hitting our websites than humans.” He emphasizes that these incidents go beyond nuisance scraping. They can drain resources, damage SEO rankings and erode brand trust.
The challenge is not theoretical. In one case, Brightspot identified multiple derivative websites that had cloned a customer’s design, hotlinked images and scripts and used AI to reword the text. The result was a copycat site masquerading as original, undermining the customer’s content ownership.
Habib advises organizations to define what “misappropriation” means for them: “First define what ‘misappropriation’ means for you — your content strategy isn’t one-size-fits-all.”
Brightspot’s Fortify solution adds layers of protection such as perimeter security reviews and anomaly detection, but Habib underscores that businesses must set their own boundaries for what’s acceptable use of their content.
Volumetric attacks: From DDoS to the clumsy burglar
The third major threat is what Habib calls volumetric attacks, which include Distributed Denial of Service (DDoS) assaults as well as automated scrapers that inadvertently overwhelm systems.
“Clumsy burglar bots may not be trying to attack you, but the result is the same: resource exhaustion,” he explains. Once costly and risky to carry out, DDoS attacks are now commoditized and easy to purchase on the dark web. That accessibility has driven a significant uptick in frequency and severity.
Brightspot customers have already experienced these challenges. In one case, a site faced periodic outages when a scraper bypassed its content delivery network and overwhelmed servers by mining paginated search results. The crawler wasn’t intentionally malicious, but the result was resource exhaustion and service disruption.
To combat these attacks, Brightspot’s architecture leverages caching and auto-scaling, while Fortify includes multilayer DDoS protections and carefully tuned WAF rules. Habib also emphasizes that organizations must extend security standards across their supply chain: “Make sure partners, vendors and integrations have the same level of care.”
Staying ahead of the curve
Habib emphasizes that there’s no “set it and forget it” solution in today’s environment. He urges organizations to take a proactive approach to defining their risk tolerance, tightening role-based access and embedding security into procurement.
“Be wary of snake oil — there’s no ‘click a button’ solution to bot control,” he warns. “The tools exist, but you have to know what you’re doing.”
Final takeaway
As Habib sums it up, every organization must view its information as a treasury — valued, protected and purpose-driven. The threats of insiders, content misappropriation and volumetric attacks may not be new, but the speed and scale at which they’re now carried out demand heightened vigilance.
By combining clear strategy with trusted partners and layered protections, businesses can stay resilient in an era where the line between human and machine-driven threats is blurring faster than ever.