Sometimes we can get caught up in the day-to-day operations of information security (tuning firewalls and making new tinfoil hats and tricking our colleagues into clicking links), and I think it’s important to occasionally step back and take a longer view of what we sometimes call the evolving threat landscape.
Here’s my two cents on that topic.
First, and most importantly, the “insider threat” remains the biggest security risk faced by any organization, hands down. If you have one priority, it has to be to focus on people’s awareness across your organization. Fortinet says that over 70% of successful ransomware attacks started as phishing — just one type of social engineering. This threat is here to stay, we aren’t doing enough, and I can’t stress this enough.
Information security threat #1: AI and the economics of social engineering
The promise of artificial intelligence is that tasks that require a human can be automated, and the quality of result will be more consistent and potentially better. Right?
Imagine that my specialty, as an evil hacker, is spearphishing — doing the research and crafting a phishing campaign targeted at a specific individual (you). I gather information from LinkedIn and your employer’s website (tenure, colleagues, boss, vendors, customers); I collect data from social media (friends, family, likes, dislikes, alma mater, vacation spots, when you take breaks); I look up info on public sources (your home value, neighborhood goings-on, new businesses opening in the area); and I sprinkle in what I can easily find on the dark web, like who you do business with and what sites you use. Then I put together a believable scenario with an effective call-to-action that will resonate with you.
Let’s say I’m pretty good at that, and so it only takes me a day or two to pull it together and launch it. If it works, great. If it doesn’t, that’s two days lost and I have to find a new mark.
That same work would take a purpose-built and trained AI about five seconds. Then it can move on to the next one, and the next, circling back to old campaigns, shutting down the ones that don’t work and improving the ones that do…
Social engineering isn’t going away; it’s about to get much worse.
Information security threat #2: Botnets by the hour
It costs less than $50 to rent an effective Denial of Service attack, and a few hundred dollars to license a proven ransomware solution. What once required the time and talent of a savvy software specialist now requires nothing more than a Tor browser and some cryptocurrency. The result is a pretty dramatic rise in the number of attacks, attacks that often have the earmarks of an amateur at the helm — which makes them harder to predict and plan for, but no less costly to manage.
Information security threat #3: Advanced Persistent Threats
Advanced Persistent Threats, or APTs, are well-equipped, sophisticated and typically state-sponsored “hacker groups” that we may usually associate with military and industrial sabotage and espionage. They have some of the best tools and talent available, and often don’t need to worry much about hiding from the authorities.
Recent trends have shown that private-sector, non-infrastructure organizations aren’t exempt from being targeted by APTs. These organizations are interesting primarily as a means to an end; as a part of a supply-chain attack, as a weaker point in a broader security perimeter, as a source of useful and proprietary information, or even simply as a convenient way to get some money (e.g., through ransomware).
Information security threat #4: Quantum computing
Quantum computing — a more thorough explanation of that here — allows the processing of information at exponentially faster rates, enabling the solving of complex problems previously unsolvable.
One example of a previously-unsolvable problem is breaking encryption algorithms like RSA and elliptic-curve cryptography, which are widely used to secure virtual private networks, emails, hard drives and blockchain cryptographic signatures (e.g., Bitcoin).
We have, depending on your point of view, anywhere from 5 to 20 years before the disruption of the internet by quantum computing, and smarter people than me are already working on quantum-resistant technologies. The thing to consider, though, is that bad actors (like APTs, above) are hoarding encrypted information that they can’t crack now, but will be able to in the future.
Information security threat #5: Copyright “drift”
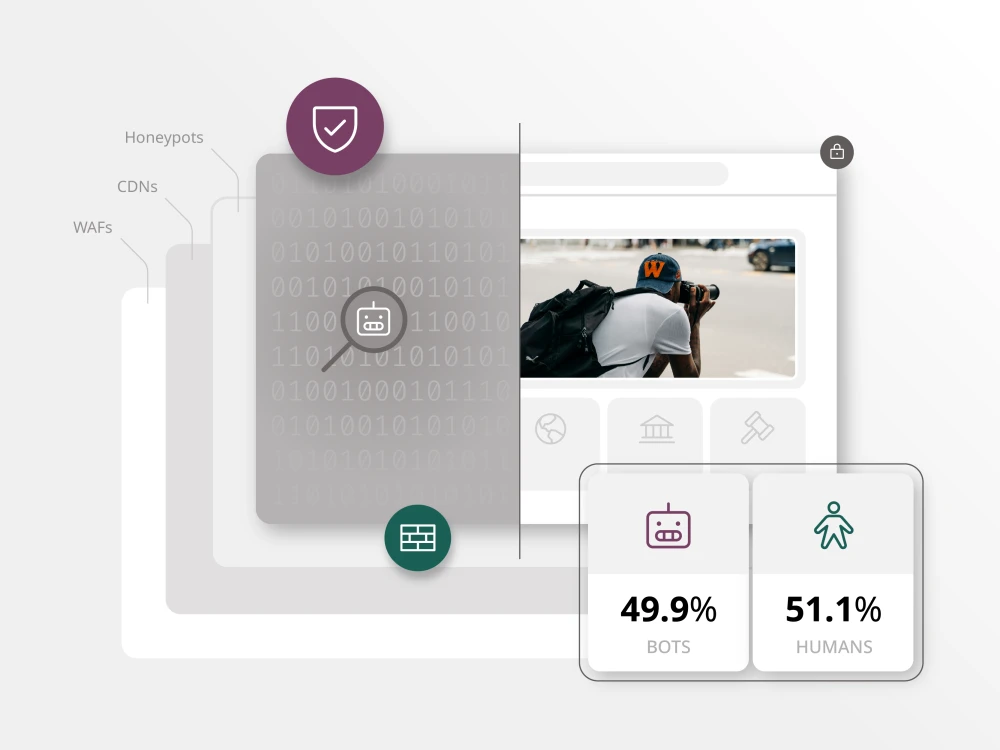
One concerning thing that we’re seeing is an increased amount of traffic to sites from “bots,” or automated data collectors, that appear to be systematically copying down entire websites for the purpose of training artificial intelligence. These bots occupy a spectrum from the fully legitimate to the purely malicious, but that’s not what concerns me.
A growing number of Brightspot’s customers are concerned about the unlicensed appropriation of their copyrighted data by third parties, or (put less gently) the piracy of created content for commercial purposes. Google answers questions using other people’s content, effectively stealing a pageview (and an ad impression or two) from the content creator. And Google is at the “legitimate” end of the spectrum. I’m not a lawyer, but it’s my impression that copyright law all over the world didn’t contemplate this kind of plagiarism — and organizations are turning to their IT and security teams, vendors and consultants for help.
It’s not all doom and gloom.
Here are 11 things you need to consider to keep your organization and data secure.
- Keep focusing on awareness and information sharing, within your organization and with other groups like customers and vendors.
- Keep pushing out sensors and turning up new monitors. Not knowing exactly what’s coming isn’t a reason to wait, it’s a reason to make sure you have as much information as is practicable.
- Access reviews! The tedious and easily-procrastinated reviews of who has access to what are hugely important. Do them more often.
- Risk assessments should be regular and theft should be the primary factor in making security investment decisions — I don’t care how cool the new shiny toy is.
- Involve the business in your risk assessment — it’s not an IT function, it’s a company priority.
- Build and maintain threat models — and use them in planning.Unpopular advice: reduce the amount of information you’re protecting. You have too much, and it’s increasing your exposure. Time to make some retention policies.
- Force the expiration of all technology, as a matter of practice. I know it still works and I know it’s expensive to replace and it’s a distraction from other efforts. You know what else is all of those things? A breach.
- Stop relying (exclusively) on generic and limited threat intelligence. IP reputation isn’t good enough anymore.
- Stop trusting that our users and colleagues will “be fine.” First, security is a team effort, and second, they’re not fine. Every organization that’s fallen prey to a ransomware attack also had a bunch of smart-well-meaning people.
- Stop taking the “narrow view” of information security. Privacy, intellectual property, ethics — all of these topics are inseparable from a good information security strategy.
A reminder, this is just one guy’s opinion. It’s up to you and your team to describe the future of information security for your organization. Let me know if I can help.